What is A Smart Security Alarm System?
A smart security alarm system is used to detect and prevent alarm situations within protective areas. Its primary function is to ensure safety by providing advance notification of potential dangers or enabling timely response in the event of an incident, thereby minimizing losses. During this process, a variety of technological means are used to compensate for the limits of human behaviors and senses, and this plays an important role in the overall security alarm system.
Typical Operating Modes of Home Security Alarm Systems
Self-Monitoring or DIY/Build Your Own
Self-monitoring or do-it-yourself (DIY) home security alarm systems are primarily based on individual monitoring, which means that homeowners take on the responsibility of monitoring their own security system.
In the case that an alarm is activated, they receive alerts and notifications directly on their own devices, like smartphones or tablets. By simply leveraging technologies like a mobile app (e.g. RB LINK app), individuals can actively monitor their homes and take appropriate actions, such as contacting authorities or neighbors, to address any potential security threats.
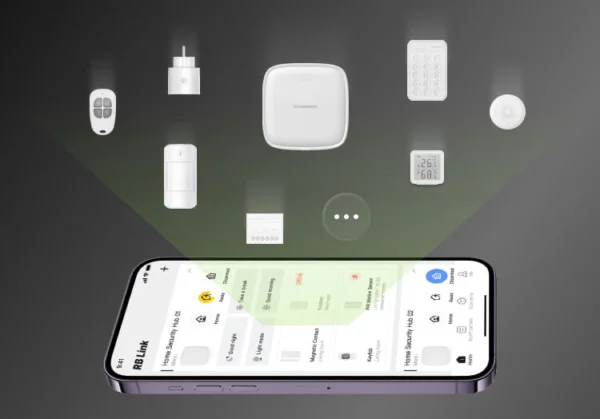
This mode of operation is commonly found in regions such as Asia and Africa.
Connect to Alarm Receiving Center (ARC)
ARC service is prevalent in regions such as Europe, North America, and the Middle East.
In this operating mode, the alarm systems installed in homes or premises are connected to a local ARC. The ARC assumes the responsibility of hosting and managing the alarm system, including handling alarm events, dispatching emergency services if necessary, and providing overall incident management.

This professional monitoring service ensures round-the-clock surveillance and prompt response to security incidents. By entrusting the monitoring and response tasks to a dedicated ARC, homeowners benefit from a centralized and expert approach to their security needs.
Commonly Seen Security Alarm Terminology, What Do They Mean?
Zone vs Area
In the realm of security alarm systems, understanding the terminology is essential. There are two terminologies that are frequently used: “Zone” and “Area” , for setting up and managing your security alarm systems in a way that guarantees thorough coverage and effective functioning.
Zone
A Zone refers to the detection range covered by a single detector. Each detector is typically linked to a single zone, and distinct locations can be monitored independently. For example, a PIR motion sensor in the living room would typically constitute one zone.
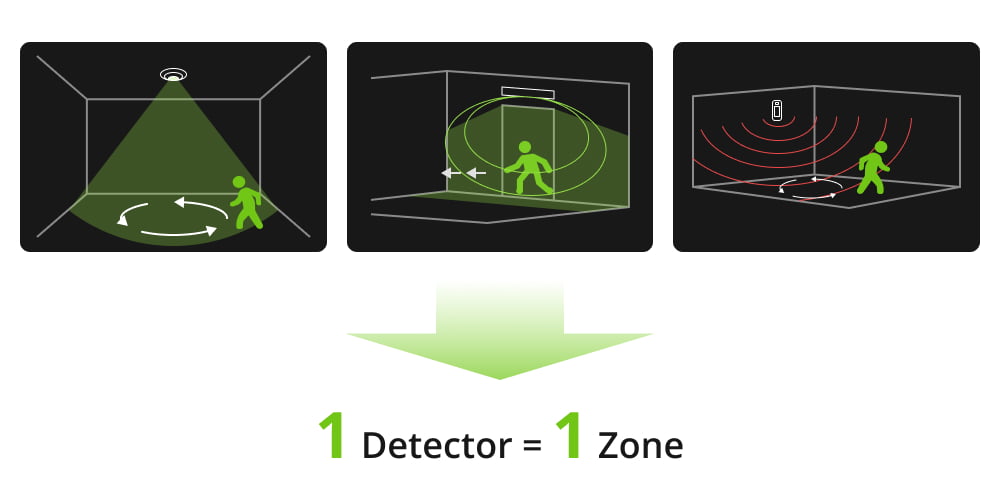
Area (also know as Partition / Group / Room)
An Area involves dividing a security alarm system into distinct subsystems that align with the physical layout of the premises. An area can consist of a single zone or multiple zones, allowing similar zones to be gathered together in a particular area of the land.
This partitioning enables customized security configurations tailored to different areas, such as setting unique arming or disarming schedules or responding according to predetermined protocols. Areas provide greater flexibility and ease of management.

Typical Zone Types
In security alarm systems, various types of zones are commonly used to define the behavior and response of the system. Having a thorough understanding of these common zone types allows for the proper configuration and customization of security alarm systems to meet your specific needs and provide effective protection for different areas and scenarios.
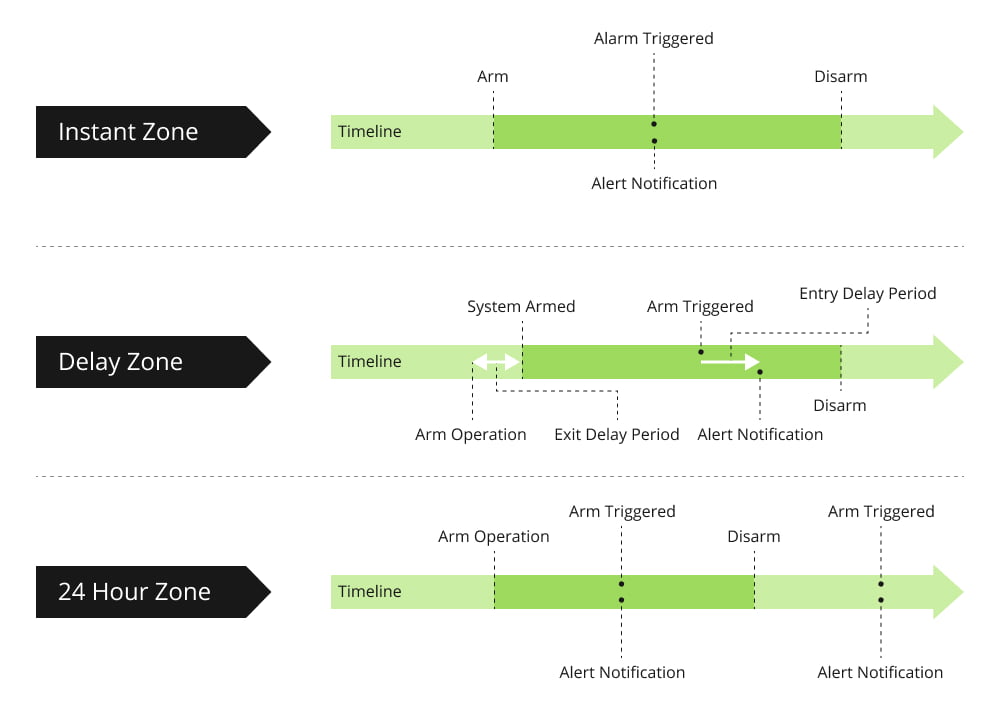
- Instant Zone: An Instant Zone is designed to trigger an immediate alert to the home security hub as soon as an alarm is activated. The majority of detectors and scenarios may be used with this kind of zone, which guarantees that any incursion or breach is quickly reported and addressed.
- Delay Zone: A Delay Zone incorporates an exit or entry delay period. Exit delay allows occupants to leave the defense area without triggering an alarm immediately. On the other hand, entry delay gives people a certain amount of time to enter the defense zone and disarm the system without setting off an alarm.
- 24-hour Zone: A 24-hour zone remains active and operational at all times, regardless of the system’s arming or disarming status. Critical situations that need for constant monitoring—like emergency alarms, fire alarms, medical alerts, and quiet alarms that sound continuously—usually fall under this category. These zones guarantee that, in the event that the system is armed or disarmed, the authorized alarms will always work and be able to cause the proper responses.
Arm vs Disarm
Understanding the concepts of arming and disarming is crucial for managing and operating a security alarm system effectively, ensuring the appropriate level of security is maintained based on the occupants’ presence or absence.
Arm
When a security system, or part of it, is in the “armed” condition, it means that it is activated and prepared to react to any inputs or sensor triggers. The home security hub is configured to execute the appropriate actions or responses based on the pre-defined settings when an area is armed. This can entail setting off alerts, notifying recipients, or starting other prearranged processes.
Arm mode can be further categorized into two main types: “Stay Arm” and “Away Arm.” When people are inside the building, the Stay Arm is usually utilized to guard specific areas while permitting unrestricted movement inside the designated zones. When everyone has completely left the property, Away Arm is used to secure every place.
Disarm
Disarm, on the other hand, refers to the state in which an area or the entire security alarm system is deactivated. The home security hub will not respond to any triggered inputs when an area is disarmed, unless certain exceptions—like 24-hour zones—have been configured to stay operational.
Disarm mode is typically used when authorized individuals are present and do not require the full security measures of the system. By disarming the system, it prevents unnecessary alarms or responses while allowing for unrestricted movement within the protected areas.
Typical Security Alarm System Devices
Security Alarm Control Panel / Hub
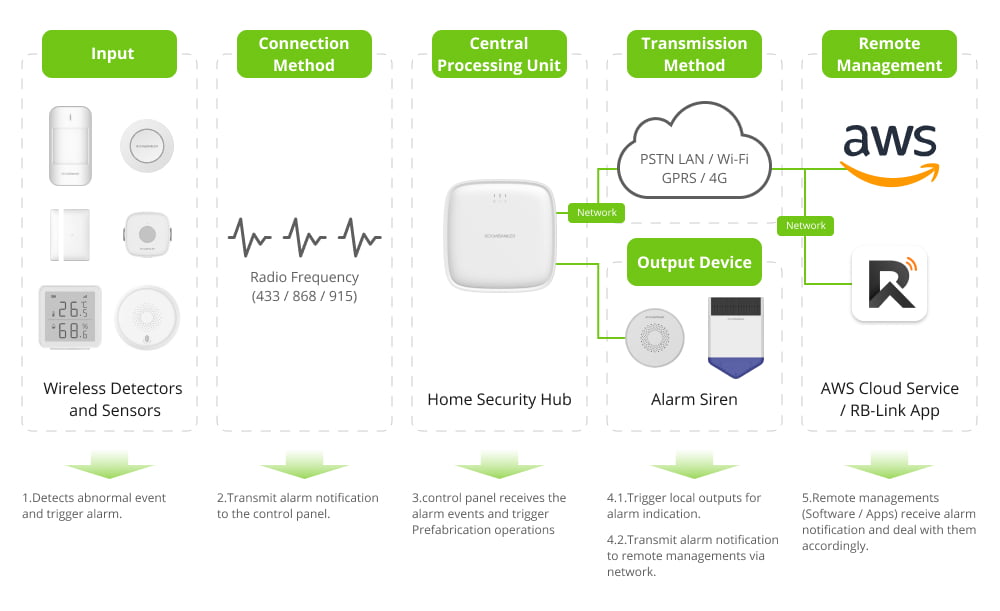
The security alarm control panel or hub is a central component of the security system that receives alarm notifications from both wireless and wired detectors when they detect abnormal intrusion events. This communication between the detectors and the control panel is facilitated through I/O signals and wireless RF technology.
Upon receiving the alarm events, the security alarm hub initiates preconfigured operations based on the programmed settings. This can include turning on local outputs to signal the alert, like alarm sirens or flashing lights or flashing lights, or transmitting the alarm notification to remote management systems via a network connection.
In the remote management mode, specialized software, such as a mobile app, plays a crucial role. It receives the alarm notifications from the security alarm hub and handles them accordingly. This can involve notifying designated individuals or monitoring centers, displaying relevant information about the alarm event, and providing options for remote management and control of the security system.
Intruder Detection Devices
Motion Sensors
Motion sensors are basic components of security alarm systems that detect movement and motion within a designated area. Motion sensors on the market use a variety of technologies, such as microwaves, passive infrared (PIR), or a mix of the two.
Passive Infrared technology operates by detecting the temperature difference between a human body and the background objects or the ambient room temperature. When a person moves within the sensor’s range, the PIR sensor detects the change in infrared radiation and triggers an alarm.
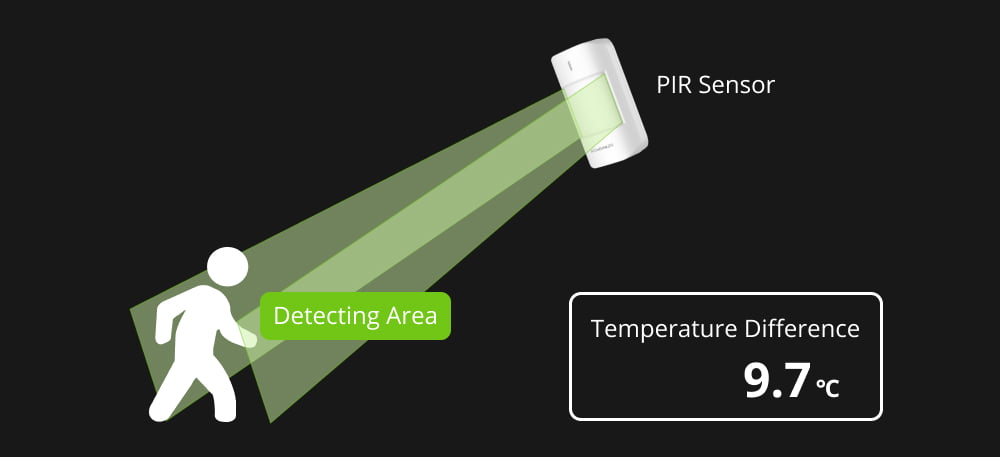
Microwave sensors, on the other hand, use movement detection through the Doppler Effect. Continuous microwave waves are released by them, and they detect the frequency change brought on by moving objects. When there is a change in the reflected signal frequency, indicating movement, the sensor triggers an alarm.
Certain motion sensors use dual-tech technology to increase accuracy and reduce false alerts. By mixing PIR and microwave technologies, such sensors lessen false alerts brought on by environmental factors or tiny animals.
Glass Break Detector
A glass break detector is a specialized device designed to identify glass windows and doors that have broken. These detectors are capable of detecting various types, structures, and thicknesses of breaking glass, and this information is typically tested and programmed into the detector’s software. There are two main detection methods employed by glass break detectors: Shatter Detection and Flex Detection.

Shatter Detection is based on detecting the high-frequency sound waves produced when glass shatters. When a glass pane breaks, it generates a distinct high-frequency acoustic signature. The shatter detection method is specifically designed to identify and analyze these high-frequency patterns, allowing the detector to recognize the unique sound profile associated with glass breakage.
Contrarily, Flex Detection is concerned with identifying the low-frequency vibrations that are produced when an object strikes glass. When a force is applied to glass, it can cause the glass to flex or vibrate at lower frequencies. These low-frequency vibrations are intended to be captured and analyzed by the flex detection method in order to identify probable glass break events.
By utilizing both shatter detection and flex detection methods, the security alarm system can detect and respond to potential intrusions or security breaches involving broken glass.
Door and Window Sensor
Door and window sensors commonly utilize a magnetic contact and a normally “closed” reed switch to detect the opening or closing of doors and windows within a security system.
The magnetic contact consists of two components: a magnet and a reed switch. The reed switch is a tiny electrical switch that, when the magnet is near it, indicates that the circuit is complete. So it is generally closed and installed on the frame or stationary part. While the magnet is usually fastened to the movable portion of the object.
When the door or window is closed, the magnet is positioned near the reed switch, keeping the switch in the closed position. This indicates that the door or window is securely shut. However, when the door or window is opened, the magnet moves away from the reed switch, causing the switch to open. This change in the switch’s position triggers an alarm or sends a signal to the security alarm system, indicating that the door or window has been opened.
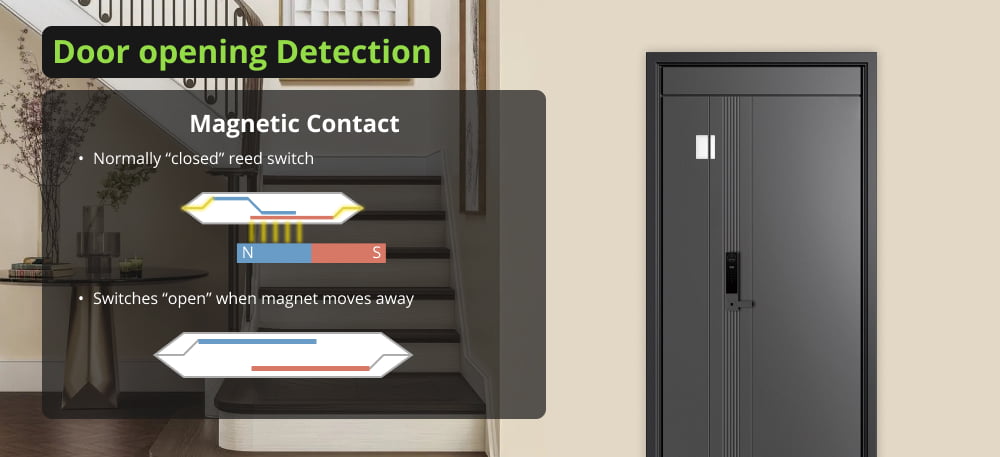
Thanks to reed switch’s normally closed design, the door and window sensor is guaranteed to be in a default state of readiness when the door or window is closed.
Water Leak Detector
Water leak detectors are designed to detect the presence of water or moisture in areas where it should not be, such as kitchens, bathrooms, laundry rooms, basements, or any other space prone to water leaks or flooding.
Usually, these detectors are placed near sinks, toilets, water heaters, washing machines, and dishwashers, or other locations where accidents involving water are more likely to happen. The purpose of their smart placement is to enable early leak detection and rapid response to alleviate any water damage and reduce the likelihood of mold growth or structural difficulties.

Security Alarm Control Gadgets
There are also some frequently utilized control accessories such as alarm keypad, key fob for the security system, tag reader, etc. They give users a local human-machine interface through which to configure and operate the system. These control accessories offer various functions and features, including:

User Authorization
The security alarm system can be configured to assign different user permissions, such as arming/disarming rights and access to specific subsystems. Then, users can locally authorize the arming or disarming of the system or gain access to particular subsystems by using passwords, swipe cards, key fobs, or other authentication techniques.
Customizable Buttons
Users can initiate linked operations or set off predefined events by pressing the customisable buttons found on many control accessories. For example, users can press a button to activate an emergency alarm or initiate a sequence of actions, such as opening a garage door or activating additional output devices.
Wireless Alarm Sirens
Alarm sirens are intended to draw attention and serve as an effective deterrent for would-be vandals or invaders, by combining loud, audible alarms with very visible flashing lights. The attention-grabbing nature of these devices can assist bring the situation to the immediate attention of those in the vicinity, notifying authorities or other concerned parties and improving the likelihood of a prompt reaction.

Indoor Alarm Sirens
Indoor alarm sirens are typically installed inside the building to warn residents and possibly frighten away prospective attackers. These sirens make sure that everyone in the building hears the alert by producing piercing, loud noises that can reach high decibel levels. They are frequently connected to the security system and activated by a number of circumstances, including wireless panic button alarms, fire detection, and unwanted access.
Outdoor Alarm Sirens
Outdoor alarm sirens are made expressly to be mounted outdoors, either in open spaces or outside of structures. They are used to notify the neighborhood or other nearby residents of a possible emergency or security breach.
Outdoor sirens are constructed to withstand outdoor conditions, including exposure to weather elements, and often feature robust waterproofing to ensure their reliability. Furthermore, some outdoor sirens have solar panels installed in order to capture solar energy, which lessens reliance on conventional power sources and improves sustainability.
We have covered a few popular security alarm devices, but this is only the beginning. There are a ton of more cutting-edge and creative options available to satisfy your unique security alarm requirements. We invite you to follow our blog updates for more in-depth information and to look through all of the possibilities accessible when it comes to security alarm equipment.
Final Word
To sum up, the purpose of this essay has been to offer insightful knowledge on the field of security alarm systems. We’ve gone over the concept of security alarm systems, clarified important terminologies, and provided a long list of security alarm devices that are frequently observed.
Roombanker is a newly launched brand led by a group of experts with deep experience in the security alarm sector. Our intention is to impart our experience and understanding to readers so they may better comprehend security alarm systems and the different gadgets that are a part of them.
By familiarizing themselves with the terminology and devices discussed in this article, we believe that well-informed readers are better equipped to make informed decisions when it comes to securing their homes or businesses.
We also appreciate the chance to work with global distributors and investigate OEM/ODM joint ventures. Please do not hesitate to contact us if you would want to explore possible collaborations or if you would like to become a Roombanker distributor. We value partnerships that enable us to reach new markets and introduce our cutting-edge home automation and security systems to more people.
Thank you for taking the time to read this article. We hope it has been informative and valuable in expanding your knowledge of security alarm systems. For more information or to get in touch with us, please contact us via Where to Buy. Our team is ready to assist you with any inquiries and provide further guidance.
